
How can I spoof my user-agent?
Have you ever thought about the traces you leave behind when you visit a website? If not, then it’s time to do so. Traces that you leave behind can in some cases lead to both safety and security risks. In this blog we discuss a specific piece of information that is sent to a website via your web browser: your user-agent. We explain what a user-agent is, how you can spoof a user-agent in an investigation and why you would want to do that.
What is a user-agent?
If you visit a website with a web browser, your web browser sends a user-agent (maybe without you knowin this). This user-agent is sent in the request header of an HTTP request and tells a web server what kind of web browser you are using. A web server now knows whether the website you visit should be displayed for a Google Chrome user or for a Safari user. Or that the website must be suitable for a desktop environment or for a mobile environment. A user-agent looks like the image below.
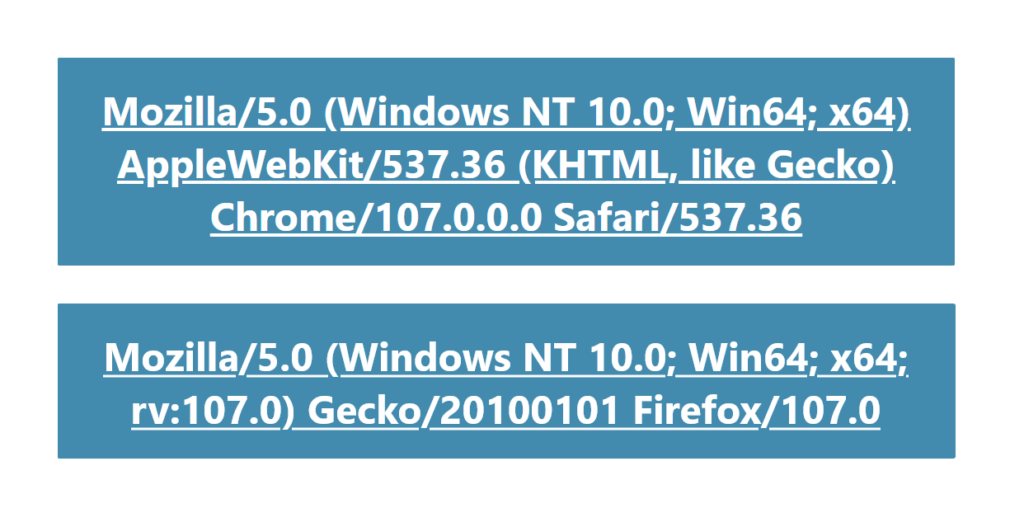
Where can I find my user-agent?
You can find your user-agent in the request headers of your HTTP requests. You can find it by clicking the key combination Ctrl+Shift+I or the F12 key. In the screen that now opens, click on the “Network” tab (see 1). Make sure to refresh the page so that all HTTP requests appear in the bar.

Now click on the first HTTP request you see (see 2), click on the “Headers” tab in the right screen (see 3) and scroll down until you see the “Request headers” section (see 4). Read there what your user-agent is (see 5). In the example below, the user-agent is: User-Agent Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:107.0) Gecko/20100101 Firefox/107.0.

How should I read my user-agent?
Now that you’ve figured out your user-agent, you probably want to know how to read and interprete it. The problem is that a user-agent is made to be read by computers, not humans. Still, if you look closely at the user-agent, you can deduce a number of things. For example, you can see in the user-agent “User-Agent Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:107.0) Gecko/20100107 Firefox/107.0” that we use a Windows operating system, a 64- bit system, the Mozilla Firefox web browser and the version number 107. Want to know for sure what a user-agent means? Enter it at https://developers.whatismybrowser.com and view the results.
Why would I want to spoof my user-agent?
Now that you know what a user-agent is, you also know that a user-agent reveals what kind of operating system and web browser you use. Of course, the more unique this user-agent is, the more you stand out as a researcher. And the fact that you stand out can cause risks, for example because the “counterparty” knows that research is being carried out. While this risk may be far fetched, it may be a reason to want to spoof a user-agent. By spoofing, we mean sending another user-agent, thus pretending to be another device. With other words, you are misleading the other party. Another reason may be that with a custom user-agent you can sometimes retrieve data from websites and social media in a different way. For example, in our module 3, we learn how to get structured data in JSON format using a custom user-agent via Instagram’s API.
How can I spoof my user-agent?
Now that you know what a user-agent is and why you might want to spoof a user-agent, it’s time to get started. In the next part we explain how you can spoof your user-agent in two ways. In the first way we do that through the functionality of the web browser itself, in the second way we do it through a browser extension from a third party.
Spoofing a user-agent through the functionality of a web browser
For this example we use the web browser Mozilla Firefox, but of course you can also use another web browser. In Mozilla Firefox, open the browser developer tools again with the keys Ctrl+Shift+I (see 1) and click on the icon of a mobile/tablet (see 2). Then click on the gear wheel that has appeared at the top and click on the option “Show user-agent” (see 3).

Now choose a user-agent (for example from this list) and paste it in the bar that appeared at the top (see 4). For example, we used the user-agent “Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/72.0.3626.121 Safari/537.36“. Now refresh the page and voila, your user-agent is spoofed. Then check again on a website like https://developers.whatismybrowser.com to see if everything worked as intended.

Spoofing a user-agent through a third-party browser extension
The previous option may be a bit cumbersome, but it works very well. Another option to spoof a user-agent is to use a browser extension. An example of a browser extension that allows you to spoof a uer agent is “User-Agent Switcher and Manager“.

If you have installed this browser extension in your web browser, you can click it next to your address bar (see 1). You can then choose a built-in option (see 2) or you can paste your own user-agent (see 2). Click “Apply” (see 3) to set up the user-agent and refresh the page for everything to take effect. Do you want to reset your user-agent? Then click on “Reset” (see 4) and refresh the page again.

Note: Be careful with third-party browser extensions!

We advise you to be very careful with third-party browser extensions. It is possible that a browser extension is malicious: in that case, the extension can capture data or break things. Are you unable to research and review a third-party browser extension yourself? Then ask for help!
More information?
In this blog we have given a short explanation of what a user-agent is and how you can check what your user-agent is. We also explained why and how you can spoof a user-agent. Of course, your user-agent is not the only data you send when you visit a website. Especially the data combined can ensure that you are posed to safety and security risks. Do you want to know more about the traces you leave behind when you visit a website? Then register for our OSINT training I (Beginner) in which we discuss this subject in detail. Soon there will also be an extensive workshop in which this is a central topic. Of course you can also contact us for more information.

